
Today we are working on Yone: 1 from Vulnhub.com, a boot-to-root from SunCSR team rated Medium Difficulty. Let’s get started.
Initial Enumeration
We start with our nmap scans.

We have ssh and http available. After a quick banner-grab attempt on ssh, I moved onto web enumeration. The homepage is fairly simple and written in Vietnamese. I tried Dirbuster with multiple wordlists, but didn’t find anything useful. Wappalyzer tells me the site uses Joomla, but a Joomscan also didn’t reveal anything useful. I think my Wappalyzer is on the fritz. I used Google translate on the website to try to find any hints, but nothing useful from that either. I shouldn’t have worked so hard…
Foothold
Running out of ideas, I thought I would try to brute-force ssh. I came up with some likely users from my Google translating of the website, kicked off a hydra session, and went to bed.

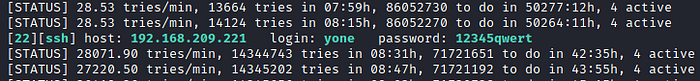
It turns out that the name of the box is our ssh user: yone. The SunCSR team is pretty well-known for this foothold so I should have guessed.
User Enumeration

After getting an ssh session to the box, the first privesc check I tried was for sudo privileges. I wasn’t familiar with Restic, but a Google search revealed that it is a backup utility. If Restic can run as root then maybe we can access root-owned files to escalate our privileges. GTFObins confirms this is possible.
Software Setup
The technique for reading privileged files via Restic requires we install some software on our attacker box. Here is a summary of what I installed:
- Go language(for rest-server) → sudo apt-install golang
- Restic → sudo apt-get install restic
- Rest-Server: https://github.com/restic/rest-server


The Restic online documentation is pretty helpful, so check it out for any issues you have with the software.
Once we have everything installed, we can launch Rest-server on our attacker box. I didn’t make any changes to the default Rest-server config, so note the default data directory and tcp port.

Reading Privileged Files with Restic
Back on the Yone box, we can use Restic to access privileged files. First we need to create a remote archive. Pick a password that is easy to remember. I chose ‘password’.

Now we use the technique we found on GTFOBins and add /etc/shadow to our remote archive.

Back on our attacker box, we can access the archive.
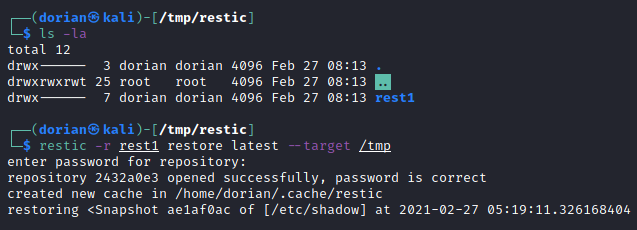
We see that Restic created an etc directory in /tmp and we have successfully accessed /etc/shadow from the vulnerable box using Restic! For the next step, also grab /etc/passwd from the vulnerable box, although you don’t need any special privileges for that.

Root Password
Since we have /etc/passwd and /etc/shadow we can combine them with the unshadow command to get them into a format to crack the password hash.

After doing the unshadow, I edited my unshadowed file to remove the service accounts and leave just user accounts root and yone. Then I used john to crack the password hashes.

Full disclosure: I initially tried to crack the hash with hashcat, something that has worked for me a number of times in the past, but unfortunately didn’t work this time. Thanks to Discord user ?????? for assuring me I was on the right track and should be able to crack the root password hash with rockyou.txt. Did you have any luck with hashcat? Drop me a comment and let me know.
Now that we have password, accessing root is trivial.

Thanks for reading!
